Email Alerts Made Easy with Microsoft Sentinel Logic Apps
Hello You,
In this article you’ll learn more on how to create a basic logic app that sends you emails for the Microsoft Sentinel generated. So, let’s get started.
Go to portal.azure.com and search for the Logic Apps azure service
And there you will find your logic apps if you had any
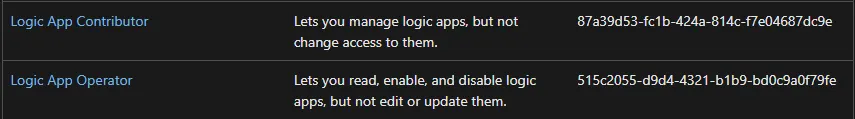
To create a new one click on Add and you’ll find many options, the standard ones requires more permissions like (Microsoft.Storage/storageAccounts/write, Microsoft.Web/ServerFarms/write, Microsoft.Web/Sites/write), however you also need Azure role-based access control roles like the Logic App Contributor and Logic App Operator, as well as Microsoft Sentinel Contributor to be able manage automation rules and playbooks in Sentinel.
Here, we’ll be choosing the Consumption logic app
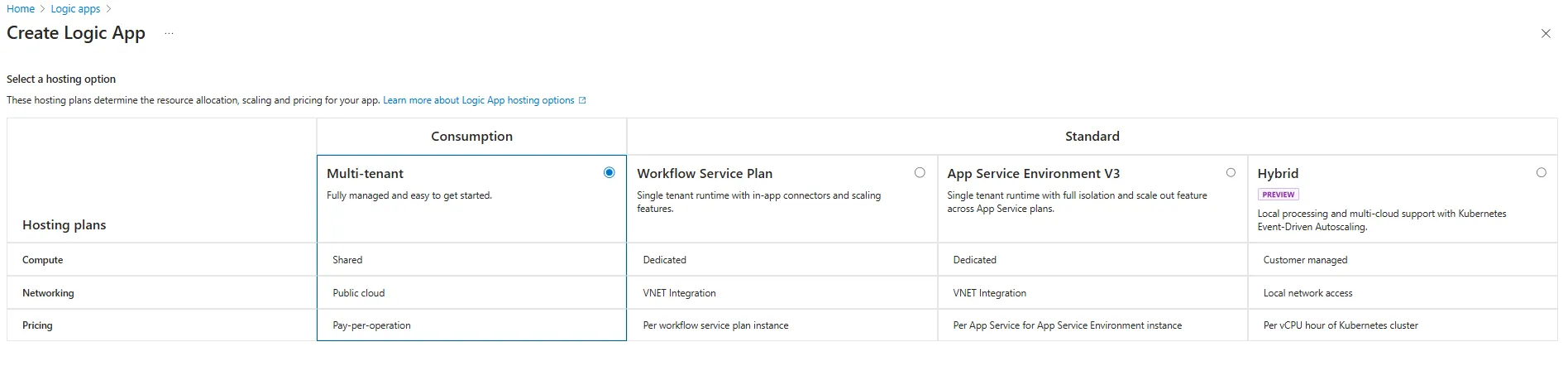
Then you need to choose the subscription and resource group and name your logic app as I named it here ElfawairTesting and choose a region that fits you.
You can add a tag if you need to, however we won’t be adding one, then just click Review + create and that’s how you will create your first logic app.
Once you open your logic app you will be faced with an overview of the logic app like the RG, location, subscription as you can see in the image
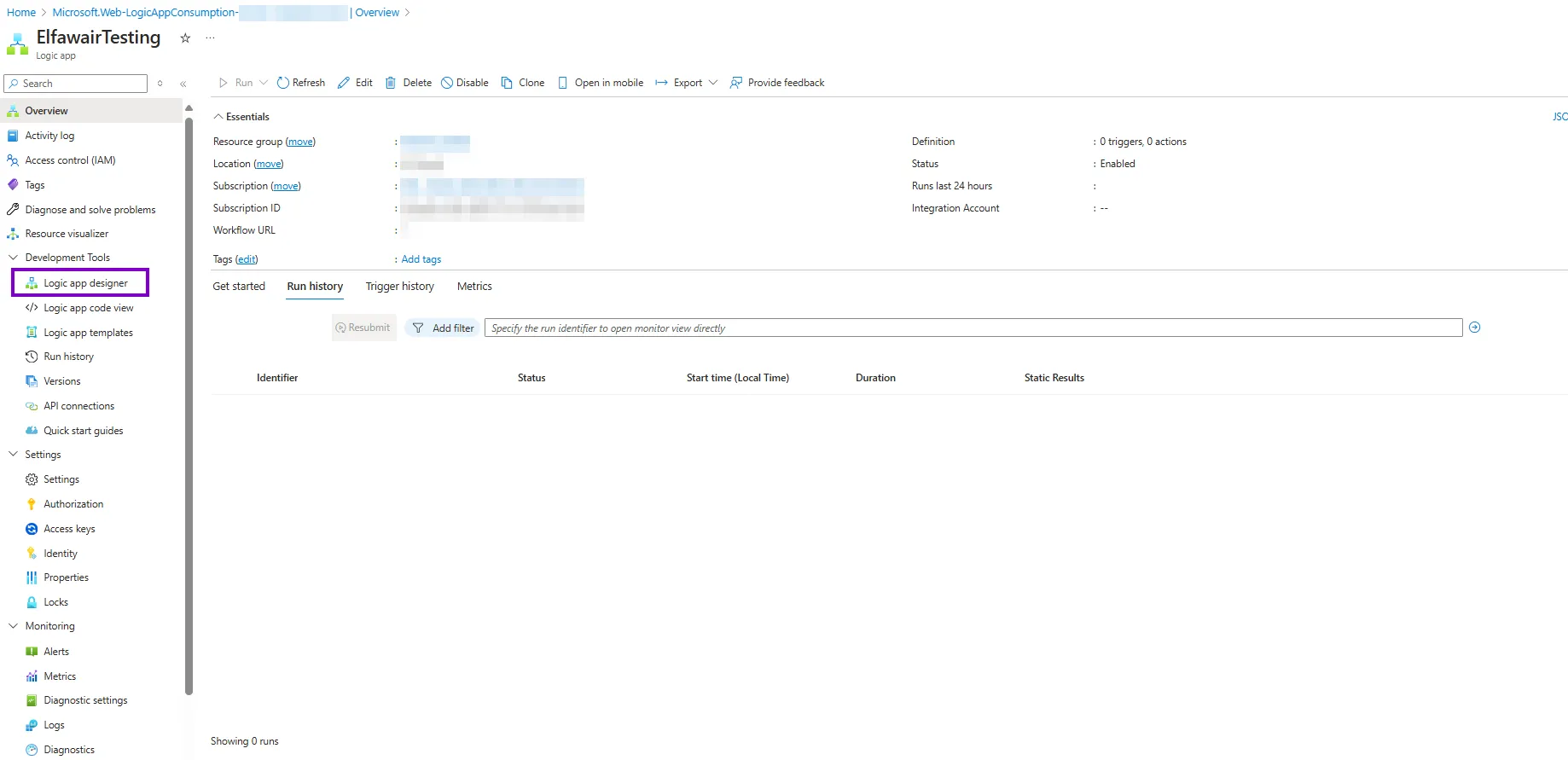
The most important part here on the left pane is the Logic app designer and the Run history as you will be using them the most while developing the logic app.
Once you open the Logic app designer you’ll see there there is nothing except the Add trigger box.
Here you need to understand that every logic app needs to start with a trigger and based on that you can add as many actions as you need.
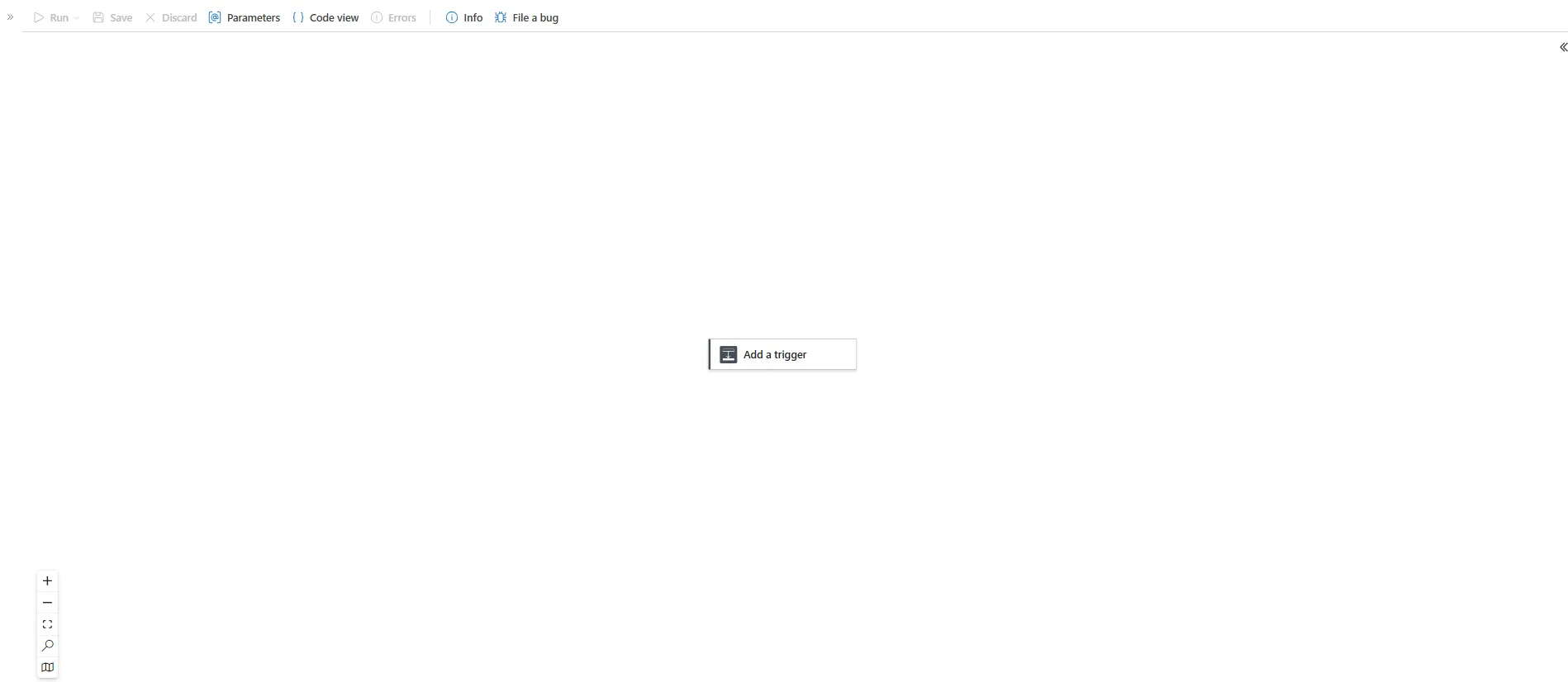
There are many triggers available, however our project today is for automating sending emails once a Sentinel incident gets generated.
we’ll be using the Microsoft Sentinel incident trigger
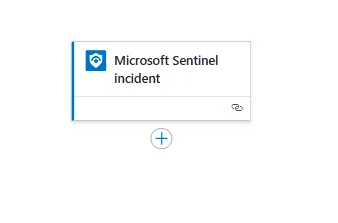
which works when a Microsoft Sentinel incident is triggered, and this playbook can be triggered by an automation rule in Microsoft Sentinel or you can just run it when an incident gets triggered by going to Actions and Run playbook
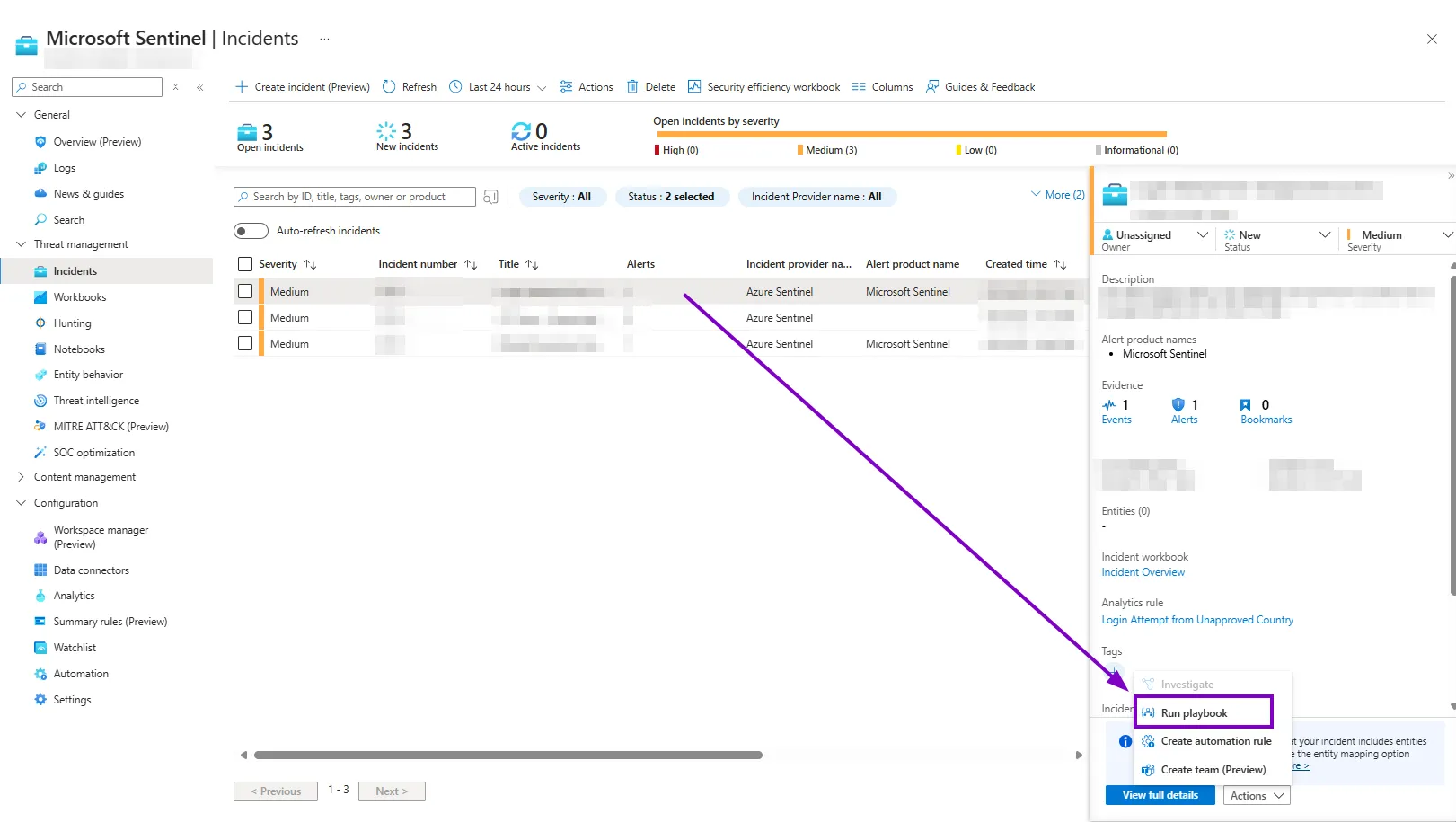
where you’ll see a list of logic apps you can run there.
Now we’ll initialize a variable that will contain the email content, I’ll ask Chatgpt to write me some HTML code for a professional email template lol

Chatgpt wrote something like this, it looks good enough.
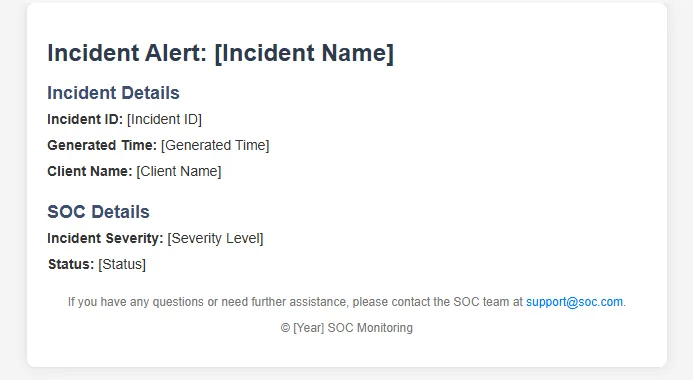
Now after creating a new action that initialize a variable for the email body we need to replace the values between the square brackets with the dynamic content from the Microsoft Sentinel Incident
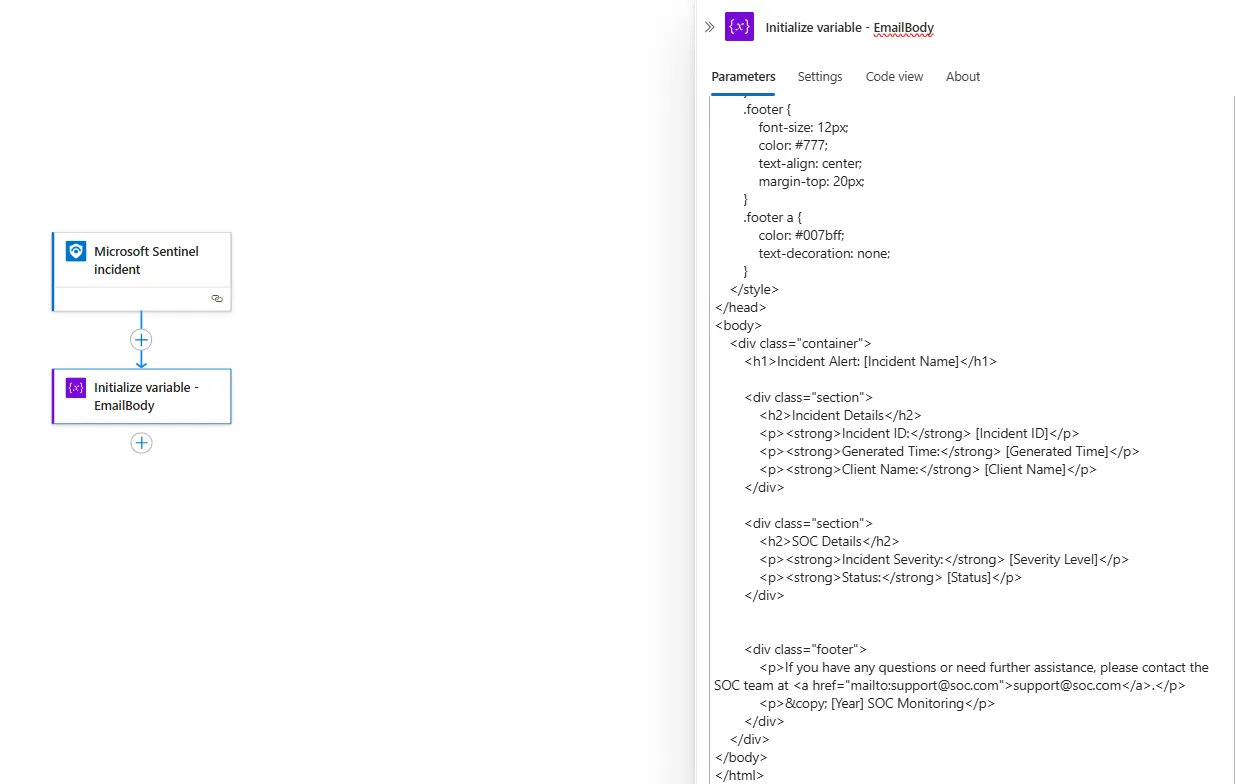
When adding a slash, we’ll see two options
- Insert dynamic content
- Insert expression
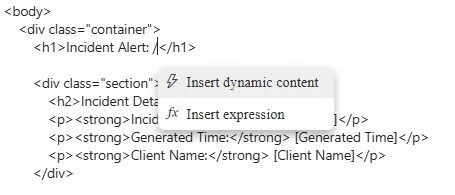
Here we’ll be inserting dynamic content, like the incident title and incident ID…
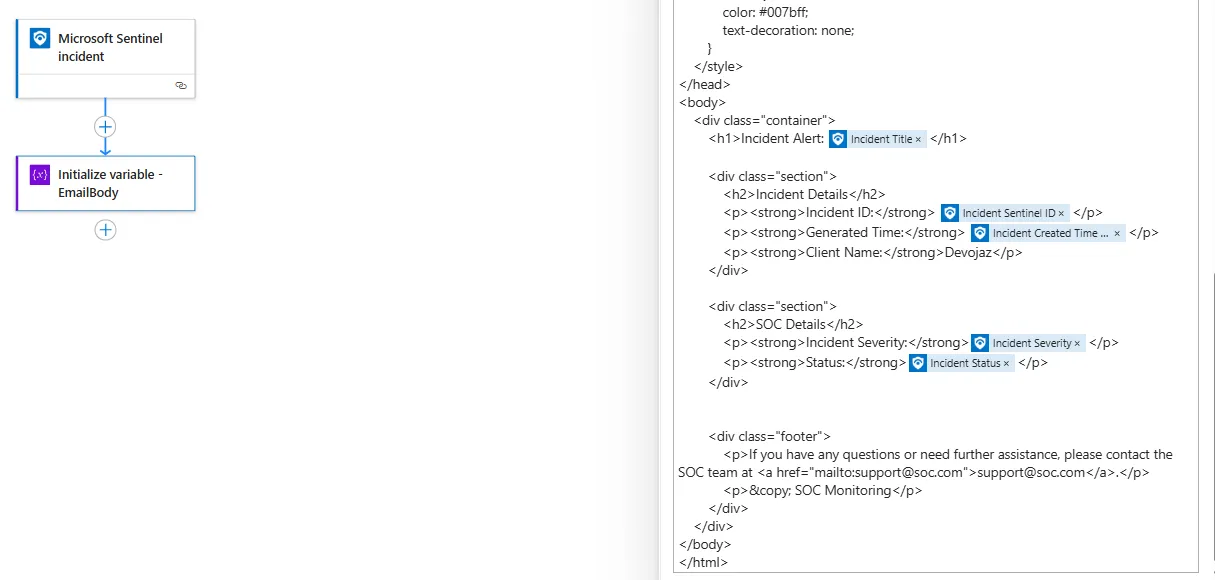
In this way we inserted everything, and the client name was hard coded.
Now we need to run the query used to generate the alert so we can get the events, and we’ll be using Run Query and list results
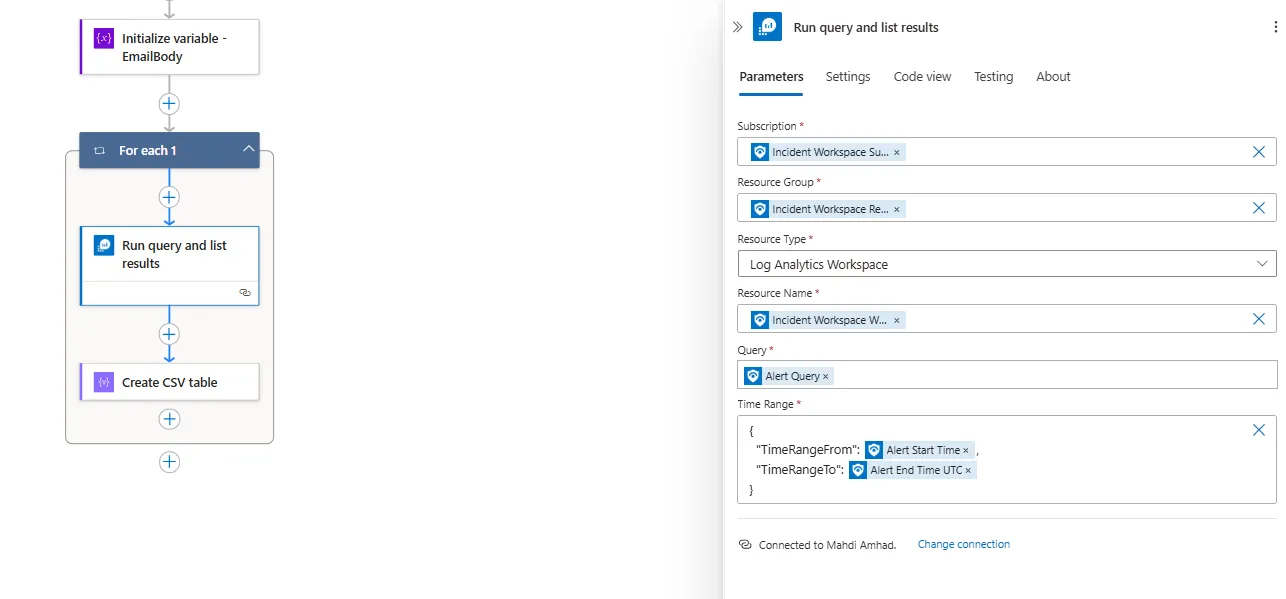
Here you can notice that we didn’t hard code the subscription or resource group, this will help later if you want to export to someone else. Additionally, we sat the time range to start with the alert start time and end with the alert end time, this will help a lot in getting only the events that triggered this alert.
Then we added Create CSV table so we can add the events as an attachment within the email.
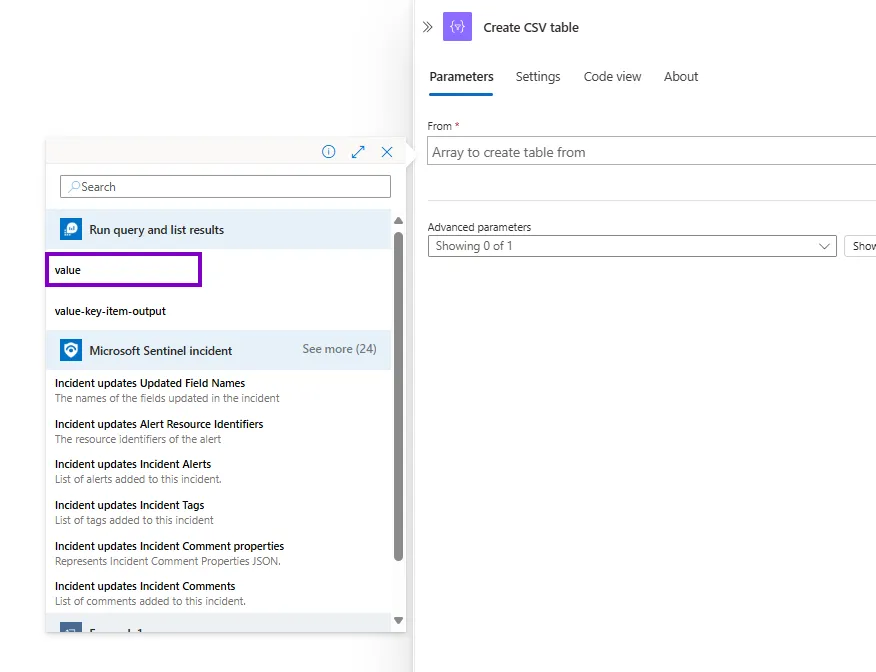
We’ll be using the value of the query that we have already ran.
Finally, we’ll be using outlook Send an email (V2) action
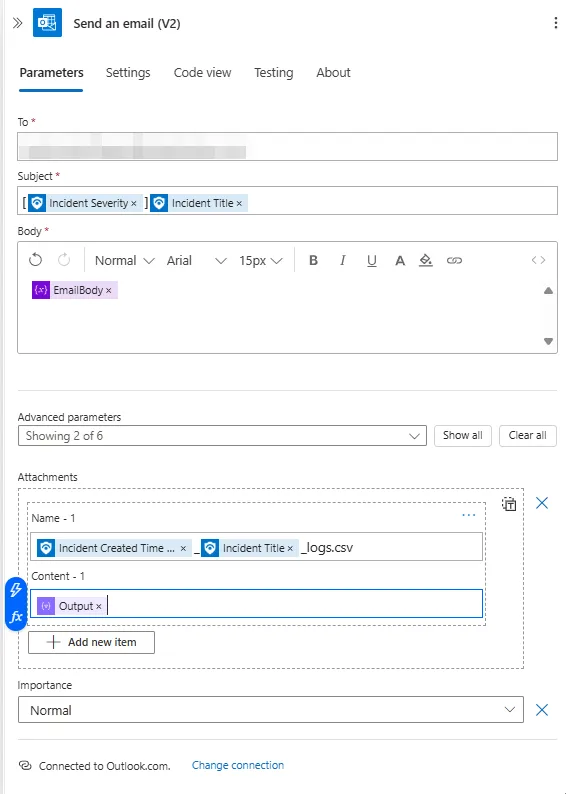
Here we set the necessary items for an email, like subject, recipients, email body and we attach the attachment as well.
Now don’t forget to save your design so we can trigger it from Microsoft Sentinel.
Now if we go to the Runs history we can check if it worked correctly or not.
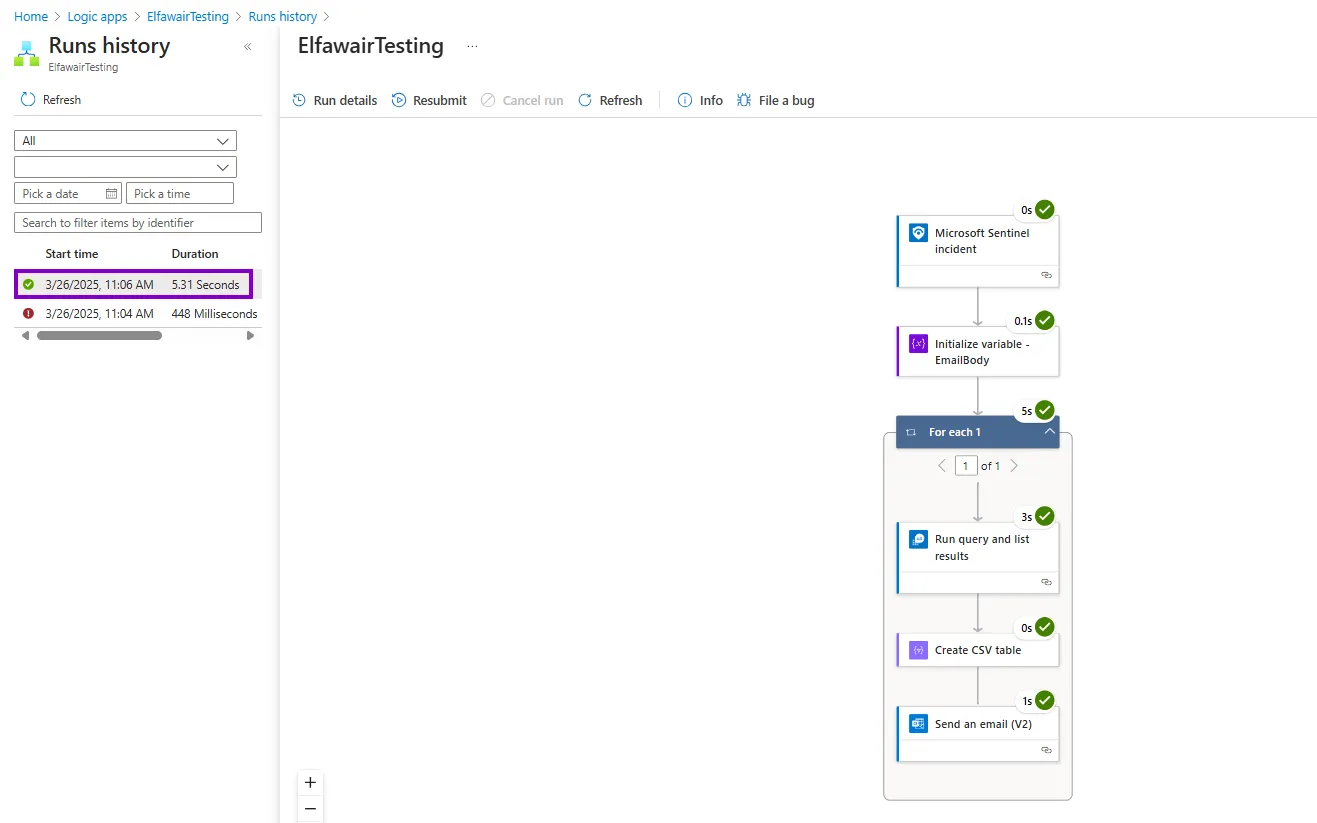
as we can see here that it did.
Now if i check my email I should have received an email.
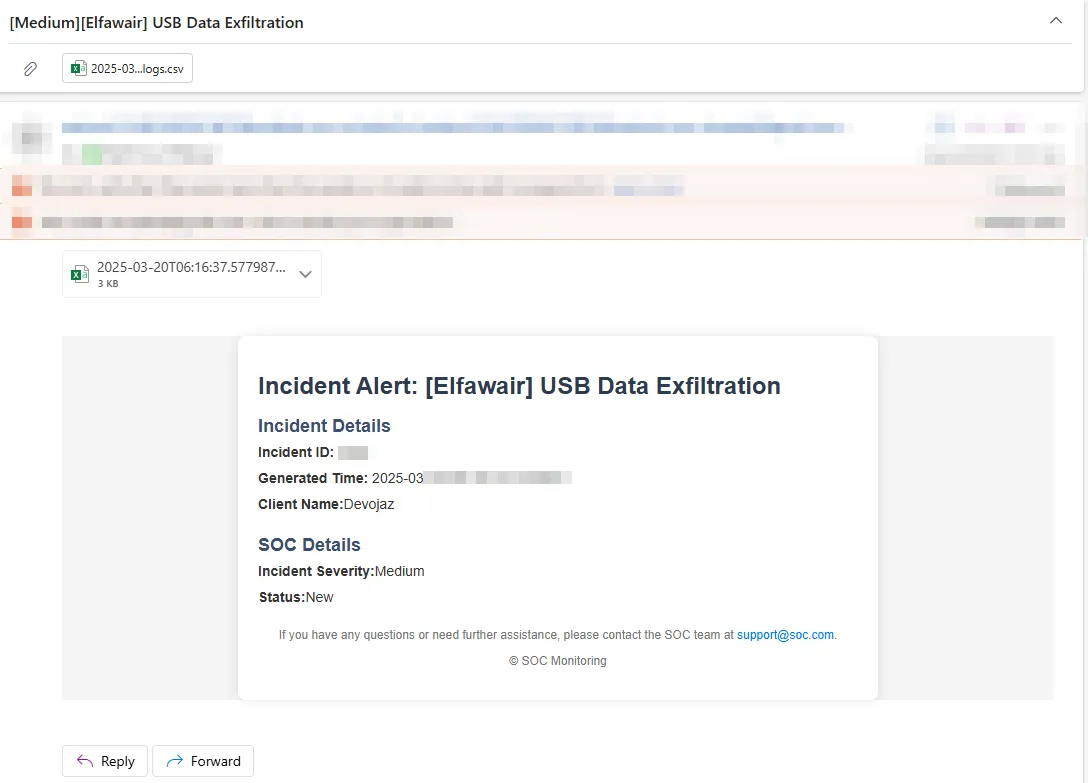
And yeah we did.
That’s how we automate sending emails to clients or to yourself with alert events, note that this can work for all kind of alerts, and it is not the best logic app, there is so many things that cloud make this logic app better like adding fail-safe events and many others.
That was it for today’s blog :)
