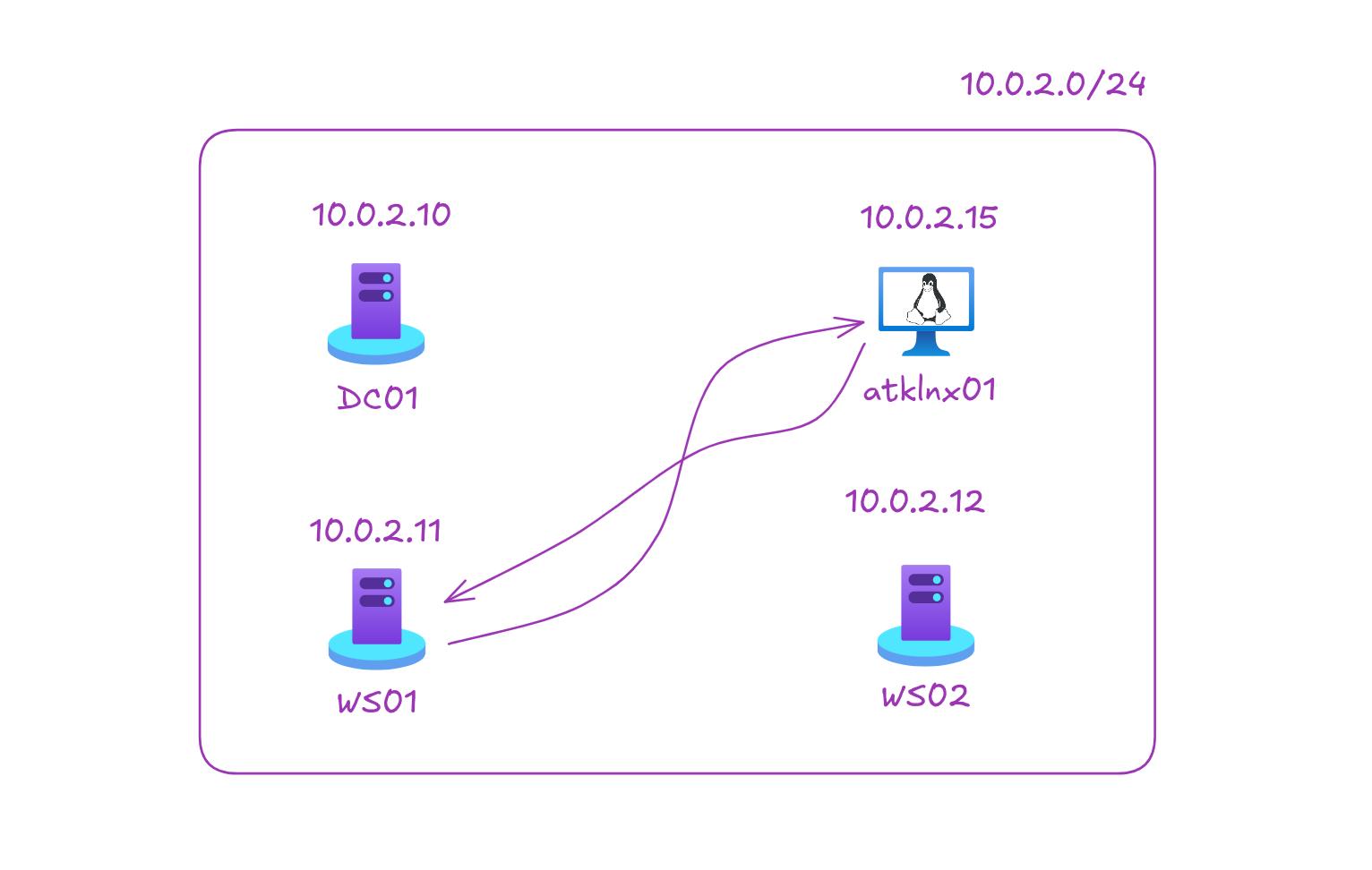
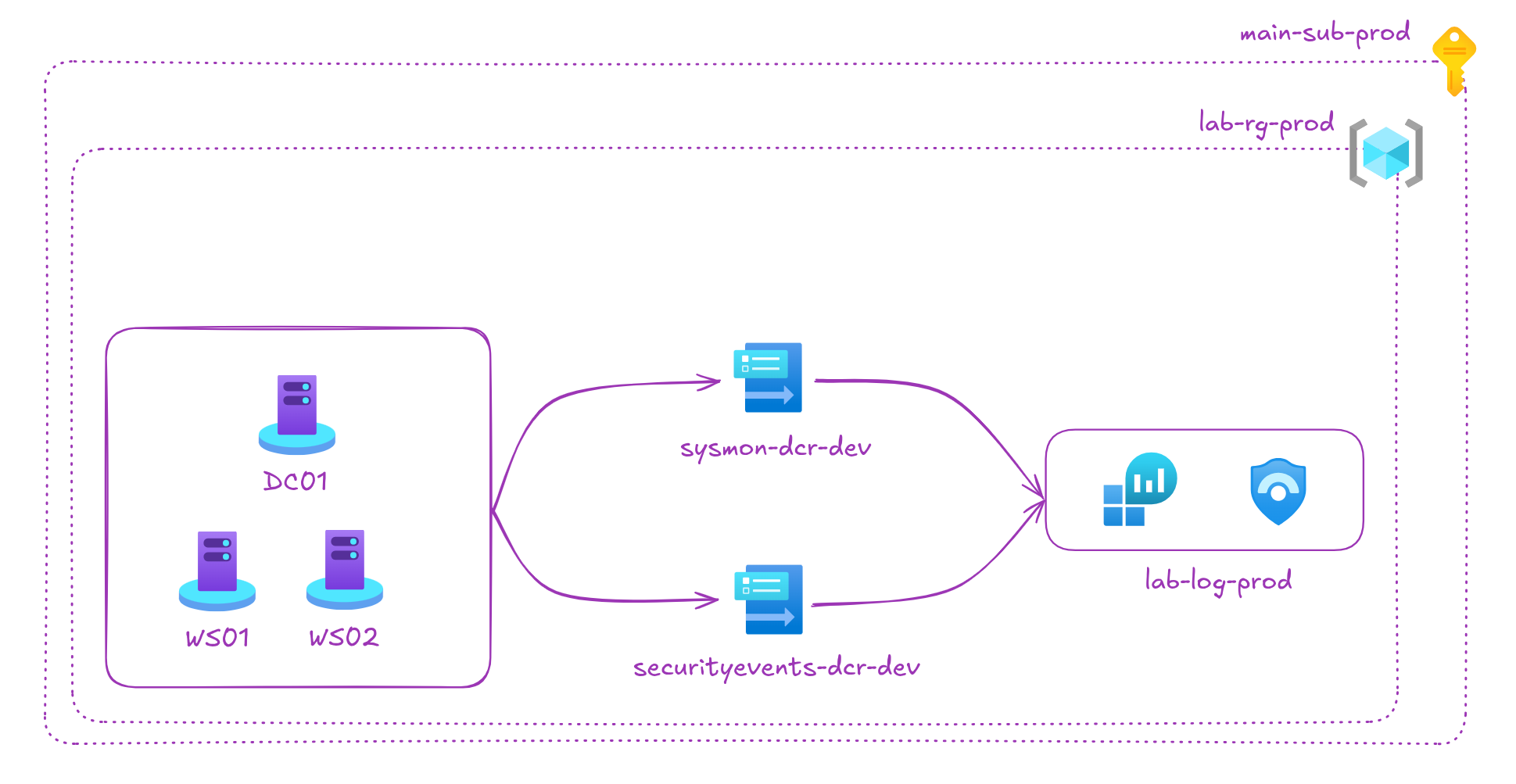
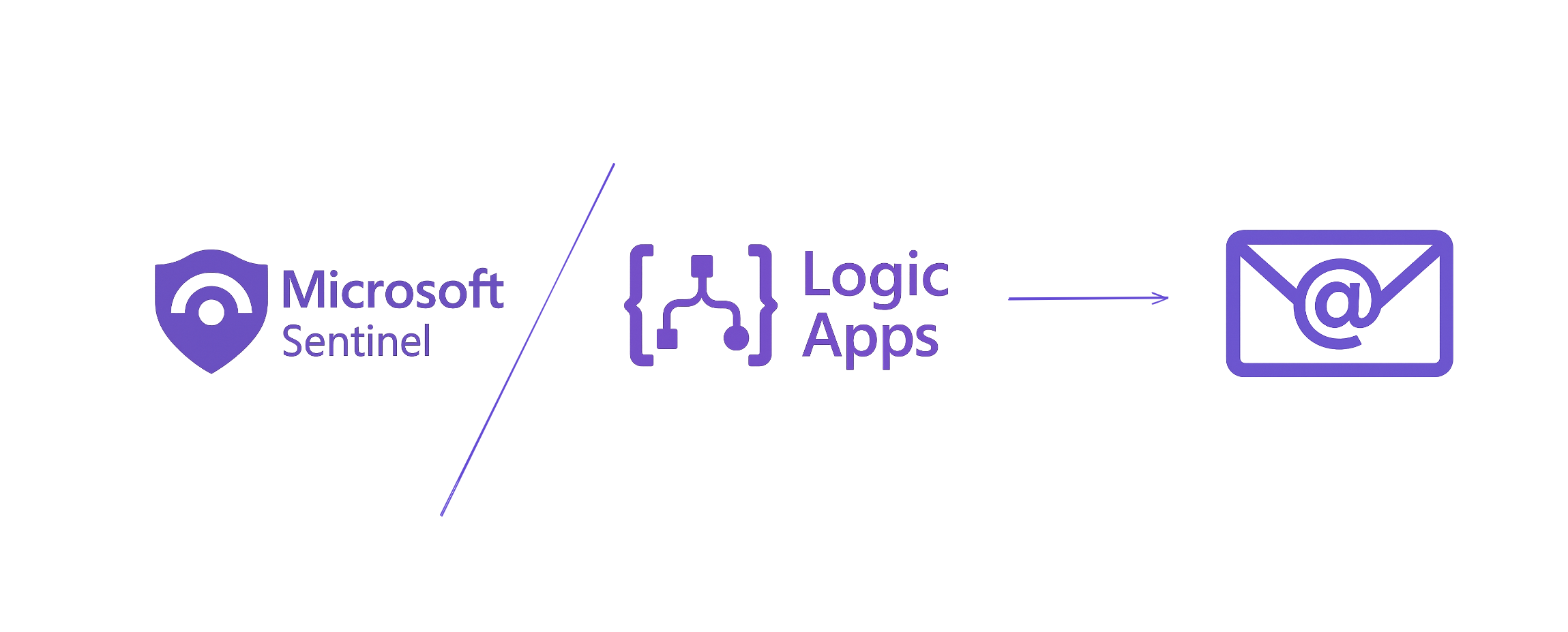
In this blog, we cover how attackers silence Microsoft Defender EDR using tools like EDRSilencer, and how to detect these attacks with key event IDs and an Azure Logic App that monitors device log activity.
The Azure Lab Diaries - Detecting EDR Silencers